












.png)

Biometrics? We all use it every day - from the moment we wake up until the moment we go to sleep. We use it to unlock our phones, access secure facilities, and even make online purchases. But what is biometrics and why is it so important?
In this blog post, we'll explore the world of biometrics and how it's changing the way we live and work. Through a deep dive into its applications, implications, and emerging trends in the digital world, you'll be sure to gain a better understanding of biometrics and how it's transforming the way we interact with technology.
Biometrics refers to the scientific practice of measuring and analyzing an individual's physiological or behavioral characteristics to identify, verify, or authenticate their identity.

Some of the most commonly used biometric identifiers nowadays are fingerprint, face, voice, iris, vein, and hand geometry.
Biometrics are categorized into two distinct sets below based on their inherent or learned attributes:
Physiological biometric identifiers are characteristics that you’re born with, such as fingerprint, face, iris, palm vein, palm print, hand geometry, and DNA. These are physical characteristics that don’t change over time and are unique to each individual, making them the most common type of biometrics used in today's world due to their high accuracy and reliability. Listed below are some widely used physiological biometric identifiers for authentication and identification:
The fingerprint is widely acknowledged as one of the most widely used biometric characteristics in our daily lives. Our fingerprint patterns are formed while we're still in the womb and continue to stay unchanged throughout our lifetime. This remarkable feature has made fingerprints a primary choice for applications that require secure identification and authentication.

With sophisticated fingerprint sensing technologies, our fingerprints can now be conveniently captured in no time at all, making fingerprint recognition a cost-efficient and reliable solution for biometric identification and authentication across many applications.
Your face is a unique combination of facial features and expressions that can easily be used for authentication purposes. Nowadays, face recognition technologies are becoming more and more popular as they're capable of recognizing a person's face in no time at all, even in challenging environments and low-light conditions.
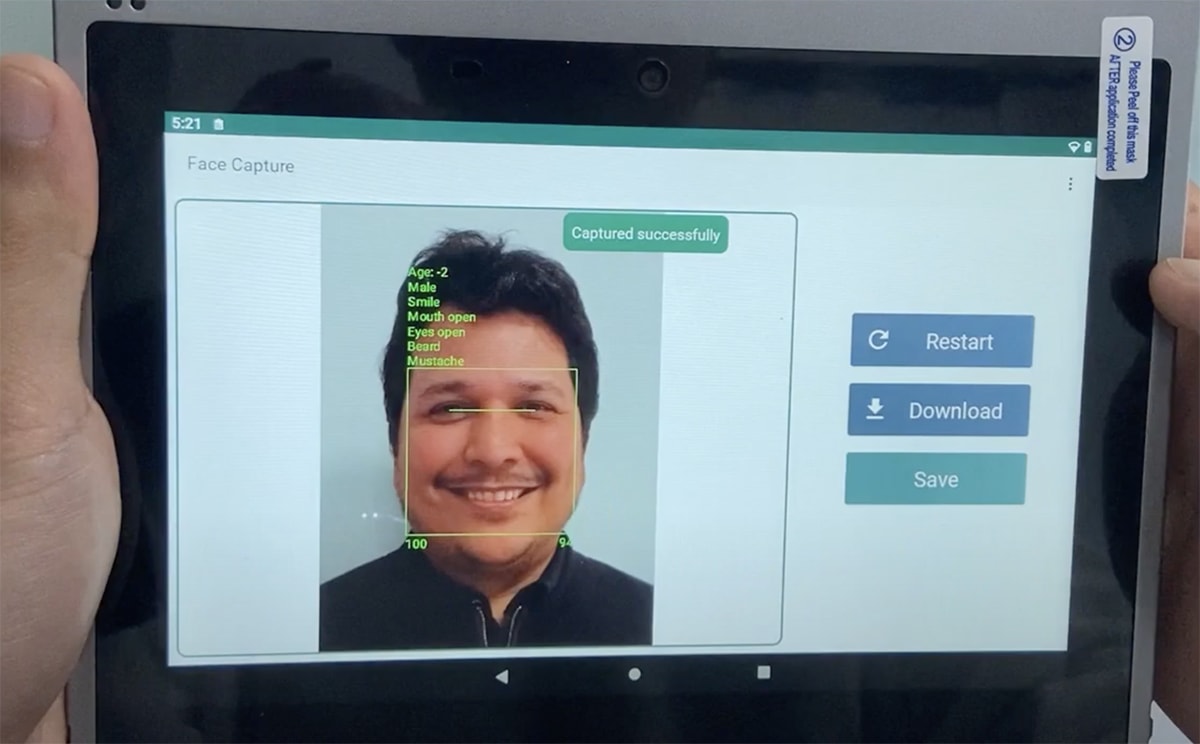
Face recognition technology has seen widespread adoption in a wide range of applications, from unlocking phones to providing physical access control and surveillance in banks, schools, airports, and retail stores. As facial recognition software and 2D, 3D, and thermal imaging sensing technologies continue to advance at a rapid rate, the accuracy of facial recognition systems is becoming more trustworthy.
The iris is the colored portion of the eye that contains several unique patterns, making it a reliable biometric characteristic. With its higher accuracy and immunity to environmental factors, such as aging and fatigue, the iris is a much sought-after biometric for identification and verification.

Iris recognition technology utilizes advanced cameras with invisible infrared light and sophisticated image processing algorithms that accurately capture iris scans for a variety of applications. It's now being utilized in banking, law enforcement, border control, etc. to provide extra security measures.
The retina is the innermost layer of the eye and contains a person's unique blood vessel pattern. Retina scanning technology uses a low-intensity beam of light to capture a high-resolution retina scan image of the eye, which is then compared against a reference database.
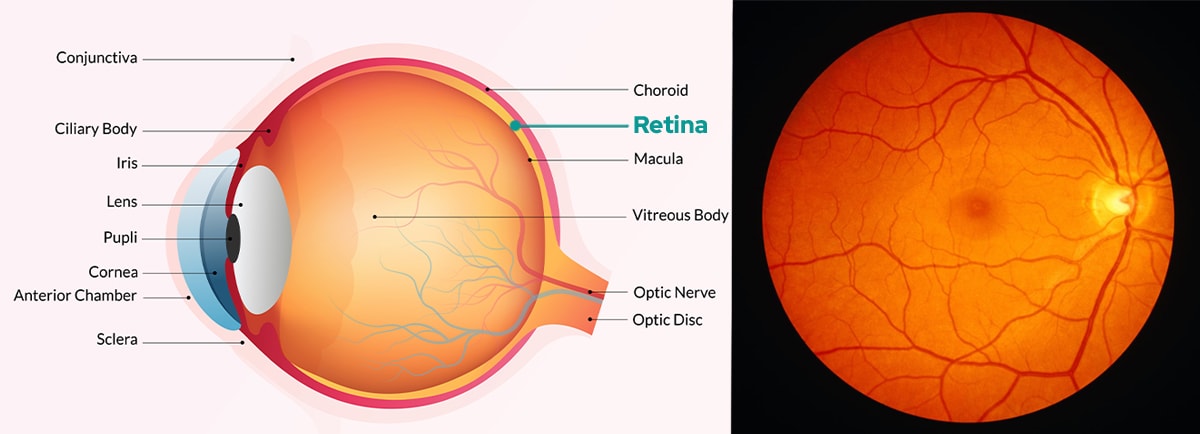
Retina scanning technology is a reliable biometric characteristic, as the pattern of blood vessels in a person's eye remains unchanged over time. This technology is now being used for high-level security applications, such as granting access to secure data centers or nuclear power plants.
Vein recognition technology uses near-infrared light to detect the pattern of veins in a person’s finger, palm, or eye, making it a reliable biometric characteristic for authentication. The vein/blood vessel patterns are unique to each person and remain unchanged over time, making them difficult to forge or imitate.

As vein recognition technology evolves, finger vein recognition and palm vein recognition are two of its primary applications. From financial services to medical care, these technologies have been adopted by a host of industries. Eye vein recognition technology is relatively new in the market, and it's being used for unlocking mobile devices.
Hand geometry is an old form of biometric data and involves making use of the physical features that make individuals unique, such as their hand size and shape. This technology involves measuring specific attributes across an individual's palm or fingers to verify identity with accuracy. Finger width, palm length, and finger length are just some examples of elements that can be used in this process for identification purposes.

Although hand geometry is not as accurate as other biometric technologies, its low cost and ease of use make it a suitable choice for certain applications. It is commonly used in time and attendance systems and access control systems.
Palm print is unique patterns to each individual and can be used in biometric authentication systems with great accuracy. Cameras are used in palm print technologies to capture a high-resolution image of the palm, which is then processed by algorithms to extract and match unique features such as the palm's lines, ridges, and creases.

This technology typically produces a pattern that is very difficult to forge or imitate, making it a reliable biometric characteristic. Palm print biometric technology is now being used in the banking and healthcare sectors, as well as public safety and law enforcement.
The heartbeat biometrics system is one of the most cutting-edge forms of biometric identification and authentication. This technology is based on a person's unique electrocardiogram (ECG or EKG) signature, which is acquired using a device that picks up the electrical signals generated by the heart.

However, heartbeat biometrics technology is still in its infancy and yet to be adopted widely. There're several limitations including the need for users to remain still and the lack of accuracy when it comes to recognizing heartbeats in noisy environments. Nevertheless, the potential of this system cannot be overlooked as it could eventually provide additional layers of security in sectors such as banking and healthcare.
DNA is the most unique biometric characteristic and can be used to identify individuals in a very accurate manner. DNA is the genetic material inherited from one's parents and is unique to each individual, making it virtually impossible to forge or imitate. It can be extracted from a person's saliva, blood, hair, or other body tissues and then compared against known samples to verify identity.

However, this technology has a number of major drawbacks including its high cost, its invasive nature, and the fact that it has a limited range of applications. Additionally, DNA analysis requires specialized training and expensive equipment, and the process can take several days or longer to complete. The applications of DNA biometrics are largely limited to forensics and law enforcement.
Unlike physiological biometric identifiers, behavioral biometric identifiers are related to the way you act or move. These identifiers are learned over time and include keystroke dynamics, mouse dynamics, gait patterns, signatures, and voices, among others. Although behavioral biometrics may not be as accurate or reliable as physiological biometrics since they can potentially be affected by stress, fatigue, illness, or the environment, they are still used in particular areas like banking and healthcare. Listed below are some of the most commonly used behavioral biometric identifiers:
Voice recognition technology uses audio patterns to authenticate users. The system records a series of vocal features such as pitch, volume, and accentuation which are used to create a “voiceprint” that serves as an individual's digital signature. Artificial intelligence (AI) and machine learning algorithms are used to match these voiceprints with the ones stored in the biometric database for authentication purposes.

Voice recognition is increasingly being used in call centers, allowing businesses to quickly and accurately verify the identity of their customers. Voice biometrics can also be used in customer service automation, access control, and secure payment systems, to name a few applications.
Gait is how an individual walks, and it can be used to create a unique biometric identifier. This technology relies on analyzing different factors such as walking speed, stride length, and body posture to authenticate a person's identity.

Gait recognition systems use cameras and other motion sensors to track an individual's walk and create a “gait map” that acts as their biometric signature. Gait recognition is still a relatively nascent technology and has yet to be widely adopted, but it is being tested in a variety of biometric security applications such as surveillance and access control systems.
Keystroke dynamics is an effective security measure that utilizes a user's unique typing pattern to identify any attempts of malicious access or suspicious online activities.

This strategy entails examining the speed and rhythm in which someone types on their keyboard, allowing it to work alongside passwords and PINs for effective two-factor authentication. It provides an additional layer of protection to online applications, ensuring they remain safeguarded from unauthorized users.
Mouse dynamics is a type of behavioral biometric that involves analyzing the speed and pattern of someone's cursor movement on a computer screen.

This technology works by tracking a user's mouse movements and then generating a “mouse map” which acts as their unique digital signature. Mouse dynamics are mainly used for user authentication and access control, as well as fraud detection in online banking.
Touch dynamics represents an advanced form of behavioral biometrics, focusing on the unique ways individuals interact with touchscreen devices. This technology captures a wide array of interactions, including taps, swipes, pinches, and the pressure applied during these gestures, to create a comprehensive profile of a user's touch behavior.

While mouse dynamics are useful for computers, touch dynamics open up new security possibilities by making apps more personal on mobile devices, providing a clear, easy method for user authentication, and keeping things safe and simple.
As its name implies, digital signature biometrics makes use of a person's unique handwriting to authenticate them. This signature recognition system requires users to sign their names on a digital tablet or a piece of paper and have their digital signatures stored in the database. Each time they need to access a particular system, they will be required to sign again and the system will match it with their stored signature to grant access.

Signature biometrics are often used in secure payment systems, allowing customers to make payments without having to provide their credit card information or PINs. It is also used in document management systems which require the signature of its users to approve transactions.
Biometrics technology brings unparalleled security and convenience to users while simultaneously safeguarding their sensitive data. With its multifaceted physiological, as well as behavioral traits, biometrics can be applied in a wide range of applications such as payment transactions, border control, biometric security systems, civil identification, benefits management, and much more. As the digital age continues to unfold, we will see a further increase in both the accuracy and adoption of biometric technologies.
Biometrics technology has deeply integrated into our lives, constantly reshaping our interaction with technology. With the advent of new advancements and increased focus on security, the biometrics market is poised for significant growth in the coming years. This section offers a detailed overview of the biometrics sector, highlighting key trends and developments as we move into 2024 and beyond.
According to the latest data from the IMARC Group, the global biometrics market reached USD 39.0 billion in 2023 and is anticipated to grow to USD 144.0 billion by 2032. This represents a compound annual growth rate (CAGR) of 15.2% during the 2024-2032 period. Such growth is supported by technological advancements, increased focus on security, and the widespread adoption of biometric solutions across various sectors.
The post-pandemic era has seen a continued demand for contactless biometrics, bolstering market growth. Consumer awareness of biometrics' benefits, such as enhanced security and improved convenience, alongside the broad adoption across government, healthcare, financial services, and consumer electronics, are key drivers of this market's expansion.

Emerging trends in the biometric industry are shaping its future, adapting to technological innovations and changing security needs. Here are the pivotal trends anticipated to influence the market:
Advancements in Artificial Intelligence (AI), ML, and deep learning are enhancing the accuracy and reliability of biometric systems. These technologies enable biometric solutions to adapt and learn from new information, thereby reducing false positives and negatives. The integration of multiple biometric modalities offers a multifaceted approach to security and identity verification.
The rising trend of remote work and online transactions has escalated the need for secure and frictionless authentication methods. Biometrics, with its unique physical attributes for security, offers a seamless solution for accessing systems and conducting transactions remotely.
The use of biometrics in border control and travel security continues to grow, providing a robust defense against identity fraud and impersonation through technologies like fingerprint and facial recognition, and iris scanning.
The demand for non-contact biometrics is growing, driven by the need for hygienic and convenient authentication methods. This trend is reflected in the increasing adoption of facial recognition and iris scanning technologies.
Voice recognition is emerging as a dominant technology in the biometrics market, offering secure authentication for devices and systems through unique voice patterns.
The market is seeing a shift towards multi-factor authentication, combining biometrics with other security measures to provide enhanced protection against unauthorized access.
Biometrics is increasingly adopted in the banking and finance sector for secure and efficient customer authentication, significantly reducing the risk of fraud.
The Asia Pacific region continues to lead the biometrics market, driven by technological advancements and the integration of biometrics in various sectors, including finance and healthcare.
Our analysis of the biometrics technology market above illustrates that these systems have now become a major player in security and authentication use cases, reaching every corner of the globe. From unlocking smartphones to providing access control or authenticating citizens for government services, it's clear that biometric solutions are highly effective. Furthermore, biometrics are rapidly being integrated into banking systems as well as sectors such as healthcare, education, and law enforcement--proving that its potential is virtually limitless.
At its core, a biometric system captures and stores biometric information from the physical or behavioral characteristics of a person, typically via a biometric sensor. It then verifies or identifies an individual by comparing this data with a reference template. It is important to note that biometric systems used in a variety of applications must adhere to three key components, which include:
Hardware components such as sensors, cameras, scanners, and other devices are used to capture biometric data. Fingerprint scanners, iris scanners, facial recognition terminals, and mobile ID devices are all examples of biometric hardware.

Biometric system software performs a variety of functions, ranging from serving as a bridge between hardware and system platforms to serving as the backbone of the system's operation, analysis, and decision-making processes, among others. The roles of software in biometric systems include, but are not limited to:
This is the repository for biometric data, typically consisting of a collection of biometric templates and other personal details from enrolled individuals. These databases are typically used as a reference library for biometric comparison during identification or authentication tasks. Aadhaar in India, the FBI's Next Generation Identification (NGI) system in the United States, the elections system in Nigeria, and the European Dactyloscopy (Eurodac) system in the European Union are all well-known examples of biometric databases.
To understand the full scope of a biometric system, it's useful to consider its working steps. From enrolling individuals to verifying their identities, biometric systems are designed to work in a number of stages:
The first step is enrollment, during which an individual's biometric information is collected and stored in the system. This process typically involves providing personal details, such as name and address, followed by capturing biometric data from the person.
Once enrolled, individuals can then be recognized each time they access a service or product. This data is typically encrypted and stored in the biometric database for future use.
During biometric identification, biometric information from an individual is compared against multiple templates stored in the biometric database. This is typically used for criminal investigations or to verify an individual's identity. The question here is "Who is this person?"
During biometric verification, a comparison is made between one set of biometric data and a single reference template stored in the database. This process typically requires an individual to enter a username or scan an ID card along with providing their biometric information. The question here is "Is this person who they say they are?"
Finally, biometric authentication is necessary for granting access to a system, account or service. This typically involves the combination of biometric data with other factors like PINs, passwords, and cards. The difference between authentication and verification is that authentication is used to confirm an individual's identity and grant access each time, while verification is used to confirm a single instance of an individual's identity. The question here is "Can this person access this system or service?"
Biometrics are rapidly gaining popularity in the digital world since they provide a robust layer of security and make it convenient for individuals to authenticate themselves. Organizations have swiftly adopted biometric systems to secure their resources, curbing potential fraud while enabling people to access their services with ease. Whether it be for banking, healthcare, or border control - the applications for biometric technology are truly limitless.
Now, let’s explore some of the most common biometric applications:
Due to the increase in fraud and identity theft, banking and financial service providers are turning to biometric technologies such as fingerprint recognition, facial recognition, iris recognition, and voice recognition more than ever before. Banks use biometrics to provide secure account access, prevent money laundering, and verify customer identities. Many banking institutions now use biometrics for a variety of jobs, including:
e-KYC is a digitalized process of validating the identity of an individual or business. To take advantage of biometrics, the e-KYC procedure encompasses gathering personal information and biometric data from easily accessible digital sources such as mobile apps, websites, or electronic documents. Banking customers' identities can be verified quickly and securely with the help of facial recognition technology, fingerprint scanning systems, or iris scanning devices, all of which help reduce the risk of fraud and speed up the onboarding process.
ATM security is critical to the protection of both financial institutions and their customers. Biometric authentication offers an even more robust security measure since it disallows criminals from accessing accounts just with stolen cards or passwords. With the facial recognition camera or fingerprint scanner at ATMs, customers can bask in a sense of peace knowing that there is an extra layer of safety alongside convenience for them as well.
Online banking is yet another area where biometrics have been applied in order to solidify security and authentication. Utilizing facial recognition technology or fingerprint scanning, customers can securely access their online accounts without worrying about potential cyber-attacks.
Biometrics are being used to increase financial inclusion and reduce poverty. Developing countries are increasingly relying on biometric authentication systems in order to provide financial services to those without access to traditional banking. Take India, for example. It has implemented biometric systems in banking sectors to provide citizens with access to financial services—much like many African countries that have done the same.
Biometrics are becoming increasingly popular in physical security systems for surveillance and physical access control. Companies, organizations, and government agencies have been implementing facial recognition, fingerprint scanning, and other biometric techniques to protect their facilities.
Biometric access control systems are being used to secure entry and exit points in schools campuses, buildings, offices, airports, banks, and other areas. These access control systems rely on the unique biometric features of an individual, including their face, iris, or fingerprint to identify and authenticate those who are allowed to enter certain areas. When combined with other credentials such as RFID cards or mobile devices for multi-factor authentication purposes, these security solutions become both user-friendly and highly secure against potential threats.
Biometrics has also been used for surveillance and monitoring purposes. Facial recognition at a distance (FRAD) is being used to identify suspicious individuals in public places, detect potential criminals, and ensure safety and security. By deploying biometric-based video surveillance systems, public places like airports, shopping malls, and train stations can be vigilantly monitored without relying on intrusive physical searches. When combined with AI and human activity recognition technologies, these systems have become even more sophisticated in spotting individuals or suspicious behavior accurately.
Biometrics is playing an important role in the public sector and government structures. It has been used for various applications such as national ID, voter registration, border control, and welfare programs. Large-scale biometric systems such as the AFIS (Automated Fingerprint Identification System) or ABIS (Automated Biometric Identification System) help governments reduce identity theft and fraud while delivering services in a more efficient and secure manner.
For instance, India has implemented the world’s largest biometric ID program by introducing Aadhaar—a unique 12-digit identification number linked to an individual’s biometric data such as fingerprints and iris scan. This system allows Indian citizens to access various government-run welfare programs and services without facing identity fraud or other security issues.
Biometric systems are being used to issue national ID / civil ID cards in many countries worldwide. These systems enable governments to track citizens and store digital records of their personal information, such as name, biometrics, age, gender, address, and more. By using biometric data-based IDs, governments can ensure accurate identification for citizens and secure access to government services.
Biometric voter registration (BVR) systems are being used in many countries worldwide to prevent electoral fraud. By relying on biometric features such as fingerprints and facial recognition, governments can ensure that only registered voters are allowed to cast their ballots. This helps to ensure the integrity of elections and reduce the chances of electoral fraud.
Governments are now leveraging biometric technology to enhance border security and streamline immigration procedures. By incorporating biometric databases, travel documents like biometric passports and VISAs, and utilizing unique identifiers such as fingerprints, photos, or iris scans to verify identities, governments are able to create a secure, reliable border control system that reduces the chances of identity fraud and illegal immigration.
Biometrics has long been used in the law enforcement sector to improve crime detection and prevention. By relying on cutting-edge biometric identification techniques, such as fingerprint recognition, facial recognition, DNA analysis, and criminal AFIS/ABIS systems, law enforcement agencies are now possible to identify potential suspects with increased accuracy and speed. Biometric data-based systems are also being used in prisons to gain more control over access and monitor inmates’ movements, thus preventing fraud and other security breaches.
Biometric systems are being used to deliver social welfare services in a more efficient and secure manner. By authenticating beneficiaries with biometrics, governments can ensure that only the correct individuals are receiving their rightful subsidies.
Biometrics is also making its way into the healthcare sector, with many hospitals and healthcare providers relying on biometric identification systems to improve patient care and reduce the risk of fraud. By using biometric data such as fingerprints, photos, and iris scans to identify patients, healthcare providers can ensure accurate medical records and provide personalized, secure health care to their patients Some of the common applications of biometrics in healthcare sector include:
The biometric authentication system is used in many hospitals, clinics, and other healthcare facilities around the world to make sure that each patient gets the right care and that their records are correct. This system is vital for attaining "Right Patient, Right Care," since it makes sure patients acquire the proper medication as well as treatment.
Biometric access control technology is used in hospitals and many healthcare facilities to restrict entry or exit for unauthorized personnel. The COVID-19 pandemic has necessitated a dramatic shift in the way healthcare institutions are managing access control. Contactless biometrics such as facial recognition and iris scanning has been adopted by hospitals to minimize contact between personnel and patients, thereby reducing the further spread of the virus.
The biometric authentication system is also being used to secure medical records and protect patient information. Through the system, hospitals can ensure that only authorized individuals have access to sensitive medical data.
In recent years, biometrics has become an integral part of consumer electronics, making mobile devices more secure and user-friendly. Common applications of biometrics in consumer electronics include:
Smartphones nowadays boast a wide variety of biometric authentication methods, such as facial recognition, fingerprint scanning, and voice/iris identification. Not only do these mobile biometrics systems make it more convenient for people to unlock their phones, but they also add an extra layer of safety to safeguard confidential information.
Biometric authentication is also being used in the world of personal computing to secure both desktop and laptop computers. Fingerprint sensors and facial recognition systems are being used more and more to keep people from getting into computers. Some systems even let multiple people log in using different biometric factors. This helps to ensure that only authorized users can access the computers, keeping personal data and other sensitive information safe from potential theft or misuse.
Biometrics technology is not new to the automotive industry, and automakers are increasingly incorporating it into their vehicles to provide safe and convenient driving experiences. Fingerprint scanners, facial recognition systems, and voice identification can be utilized for entry unburdened by traditional keys. You can also have access to other in-vehicle features, such as driving modes or infotainment systems, with just your unique biometric data.
Biometrics have soared in popularity over the past few years, being utilized for banking, consumer electronics, and more, as we discussed above. But why should we use biometrics? What advantages does it bring us? To gain a better insight into the capabilities of biometric technology, here are some of its advantages, which may encourage you to give it a try:
When we bring biometrics into the conversation, security is usually top of mind. Biometric identification and authentication are based on individual physiological or behavioral biometrics, which makes it a more secure alternative to conventional methods such as passwords and pins. These biometric identifiers used for recognition are hard to replicate, providing reliable security measures that can't be breached easily.
With biometric systems, users no longer have to waste time remembering or storing credentials - they can simply utilize their unique identifiers such as fingerprints and facial features for immediate access. This not only makes accessing accounts or devices easier but also much more convenient than conventional methods.
Another advantage of biometric systems is that they can be used for large-scale projects. For example, airports now use facial recognition systems to speed up the boarding process. This saves time and resources, as it eliminates the need to manually check each passenger's identity documents.
Biometrics can be easily incorporated into any online service or mobile application, providing organizations the feasibility to authenticate identities from anywhere. This not only makes it more convenient for users and providers but also elevates digital services' management capabilities. Many African countries, including Ghana and Nigeria, have embraced biometric technologies combined with digital ID infrastructure as a solution for preventing financial fraud and improving financial inclusion.
Biometric systems are cost-effective in the long run due to their long-term maintenance costs being lower than those of traditional methods. For example, with biometric access control systems, there is no need to replace cards or keys whenever an employee leaves the business. This makes them a great investment for businesses and organizations looking to streamline their operations, as well as improve their security measures in the process.
As we can see, biometrics offers numerous advantages, making it a great identification and authentication solution for both businesses and individuals. We are seeing an increase in the adoption of biometrics technologies in various industries such as government and finance, ushering us into a new era of digital identity in which biometrics are the rule rather than the exception.
Despite the numerous advantages of biometric systems, there are still some challenges and disadvantages that should not be overlooked. To gain a better understanding of these, here are some of the key challenges to take note of:
The use of biometrics for authentication is based on the collection and storage of sensitive data, which can potentially lead to privacy concerns. For example, if organizations store their users' biometric information without their consent, they are essentially violating those users' privacy. This may result in identity theft and other malicious activities. This is especially worrying for biometric data, which is permanent and can't be changed as passwords can.
To mitigate this risk, organizations should implement stricter guidelines and protocols, such as user consent and data encryption, to ensure that information remains secure and is used ethically.
False Acceptance Rate (FAR) and False Rejection Rate (FRR) are two key performance metrics used to assess biometric system accuracy. FAR measures how frequently a system accepts an imposter by mistake, whereas FRR measures how frequently it rejects an authorized user. While various factors, such as the quality of biometric data and the algorithms used to process it, can influence FAR and FRR, these metrics should not be overlooked because they can have a direct impact on the system's accuracy and overall performance.
To reduce the chances of false acceptance and rejection occurring, organizations should use multi-factor authentication methods that combine biometric data with other forms of authentication factors, such as cards or QR codes. This will help ensure that only authorized users have access to the system and can prevent potential unauthorized access.
Biometric spoofing is a technique used to bypass biometric security systems. It involves creating fake fingerprints or images of a person's face in order to gain access to restricted areas. Organizations should be aware of the risks associated with biometric spoofing and take appropriate measures to ensure their systems are protected.
An efficient method is liveness detection, which checks to see if the biometrics collected actually come from a living person rather than a fake or fabricated one, or which asks users to perform actions like blinking or speaking to verify their authenticity.

Despite these challenges, biometrics remains an important and effective tool for identifying and authenticating individuals and is likely to become even more prevalent in the future. With the right measures in place, organizations and businesses can securely leverage biometrics technologies and reap the many benefits it has to offer.
Biometrics is an effective tool for identifying and authenticating individuals, and its use is only likely to become more widespread as technology advances. Although there are some challenges associated with biometrics, these can be addressed by implementing the right security measures and protocols. With so many applications for biometrics, it is clear that it has the potential to revolutionize authentication and revolutionize the way we access and manage our digital lives.
By leveraging biometrics, organizations and businesses can create a secure digital environment that is both efficient and user-friendly. Ultimately, biometrics technologies can help to create a more secure digital future, one that is safer and more reliable. Do you have any questions about biometric authentication? Contact us now! We'd be happy to help.
.png)